Deep Freeze Reboot to Restore Software provides ultimate endpoint protection by freezing a snapshot of your desired computer configuration and settings. With an instant reboot, any unwanted or unauthorized changes are completely erased from the system, restoring it back to its pristine Frozen state. Apple introduced the APFS file system in High Sierra and Faronics Deep Freeze Mac now supports APFS formatted file systems! New Features - Support for macOS 10.13.5 or higher. Deep Freeze Mac has changed the way IT Professionals approach end-point security; its non-restrictive concept offers the most robust Mac protection available.The need for IT professionals to perform rebuilds, re-image, or troubleshoot computers is eliminated with Deep Freeze Mac ARD reboot-to-restore technology. With the release of Deep Freeze Mac 7.x we Deep Freeze Mac is currently able to support Fusion Drives on systems that are running Mohave and have the APFS file system configured on the Fusion Drive.
When you use Faronics products, you entrust us with data regarding your system and your system’s users. We recognize that your privacy and security are valuable, and that in collecting and holding your data we have the responsibility to use it responsibly and keep it secure. To ensure your privacy, we use your data only to provide you with services and to improve those services. To ensure your data security, we ensure the data is stored on secure servers, and erase it when you no longer require our services.
Below is an explanation of why we collect your data, how we use it, how long we keep your data, and what types of data we collect. If you have questions about what you see here, don’t hesitate to contact us at dpo@faronics.com.
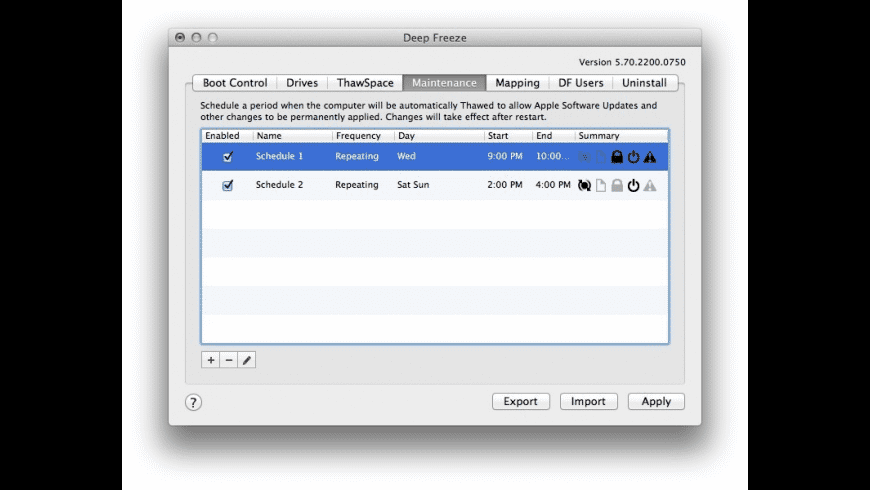
Deep Freeze Install
Faronics Deep Freeze Mac
Faronics’ products enables our customers to monitor and control user computers and mobile devices, and as part of this process, our software collects and analyzes data regarding hardware and software configuration, and user activities. The data collected by the software is essential to its operation and its continued improvement. Simply put, Faronics software requires a fair degree of knowledge of the current and intended states of target systems to safely execute commands on them, and requires knowledge of user actions to effectively monitor what target systems are doing. This data is also used to help inform decisions regarding future improvements to the software, including how to improve user experience, what new features to develop, and what issues require correction. Faronics does not use system configuration or user data to create targeted advertisements.
Faronics software also collects data regarding our customers, which is used to maintain our relationships with those customers. Customer data is not used to create targeted advertisements.
Deep Freeze Cloud and its services are deployed using a cloud model, where software is deployed on a cloud and maintained by Faronics staff. While the customer has control over the configuration and actions of the software, Faronics acts as the data processor on the customer’s behalf. Data is collected, processed, and stored using our servers, and is subject to Faronics data security and privacy policies. That said, customers have access to the processed data and much of the raw data, and can export some data types to their own system if they choose.
Although Faronics software is used to collect data, Faronics itself does not interact directly with the end users, who are the customers of Faronics’ customers. Rather, the software is managed by Faronics at the customer’s behest. It is therefore the customer’s responsibility to ensure that they have consent to collect data from the end users.
- In addition to our regulated responsibilities, Faronics is committed to following best practices in privacy and data protection. Faronics retains a subset of the data it collects, and will retain your data for as long as necessary to provide our services to you. When the data is no longer required in order to deliver services, and after suitable notice to you, we will delete your data from our system. Generally, this is within 12 months to 2 years of you no longer using our services. This delay meant to provide you with ample time to safely remove the cloud clients from your environment, as the clients cannot be removed after we have erased your data. Note that you may request that Faronics remove your data sooner if you choose. For more details, please see our Terms of Service.
- UserVoice is third-party feedback collection tool that is incorporated into the Deep Freeze Cloud Console. It collects and retains data differently than the Faronics products it is a part of; UserVoice does not collect any data until the user enters feedback, at which point a UserVoice account is created for the user based on the personal information they enter. UserVoice accounts and associated data are erased when the user account is deleted, but Faronics can also delete the data at any time upon request.
- Faronics respects your privacy; we will not use your data to target you with advertisements. For more details, please see our Privacy Policy.
Faronics cloud products do not have the same data for all systems and users—what data we collect depends on which applications and services the customer has elected to use. In addition to identity, version, licensing, and configuration information of the Faronics products in use, our products have access to the following information according to each service:
Cloud Agent enables communication between the Cloud Console and the cloud services. This means that if a computer runs any cloud services, it must also run the Cloud Agent.
To perform its duties, the software requires the following data:
- Information that helps to unambiguously identify the computer, including its name, type, OS information, status flag, system locale, MAC addresses, internal IP addresses, and generated identifiers such as its Machine ID.
- The computer’s network identity and information regarding how it connects to network, including its fully qualified domain name, NetBIOS name, domain/workgroup name, and the active directory /OU name, if applicable.
- Basic user information, including who is currently logged in, who has been using the computer in the past, and when they used it.
- Faronics group and policy information.
- Additional information, including what version of .NET is installed.
Incident Reporting is a tracking utility which assists users to reduce bullying by cataloging issues and helping to recognize trends. To perform its duties, the software requires the following data:
- Information that identifies the user, including user name and computer name. Note that if the software is configured for anonymous reporting, this information is not collected.
- Details of reported incidents.
Anti-Executable prevents unknown or undesirable programs from running on computers. To perform its duties, the software requires the following data:
- Who is attempting to run executables on the computer, and what they are attempting to run.
- What executables the user is allowed to run, including their name, publisher, and hash value.
Anti-Virus detects, identifies, and quarantines malicious code. To perform its duties, the software requires the following data:
- The version of the software, and how up to date to date its virus definitions are.
- What anti-virus protection measures are currently enabled, including firewall status and active protection status.
- When was the last time the computer was scanned and when the last virus was found.
Campus Affairs is a mobile app that aggregates campus news and information for students. To perform its duties, the software requires the following data:
- Displayed text and any URLs associated with news items, courses, and notifications added to the app.
- Information regarding scheduling, including academic season dates and event calendar URL.
- Staff profile information, include names, titles, bios, email addresses, and photographs.
- PDF documents uploaded to the app for distribution.
- Customised app configurations, including name, logo, home screen, and descriptions.
- Details of incidents reported and messages sent to the administrators through the app.
CloudSync enables users to securely access and edit their cloud files even if Deep Freeze is installed on their computer. To perform its duties, the software requires the following data:
- Information regarding the computer’s software license.
Data Igloo is companion software to Deep Freeze which allows select files to be updated and saved even when Deep Freeze is active. To perform its duties, the software requires the following data:
- An inventory of all redirected files, profiles, folders, and registry keys.
Deep Freeze “freezes” the computer configuration, returning it to the same state upon reboot regardless of what occurred in the meantime. To perform its duties, the software requires the following data:
- Information that helps to unambiguously identify the computer, including its computer name, MAC address, baseboard serial number, BIOS details, CPU details, workstation ID, video controller information, and UUID
- Network connectivity information, including the computer’s IP address, domain, subnet, and network adaptor details.
- An inventory of drives and additional drive information, including drive serial numbers, volume information, partition information, disk drive and system drive details.
- Select computer configuration information, including standard and daylight saving time settings, and Windows Update server URL.
Deep Freeze Cloud Console is the interface used by administrators to manage the deployment. To perform its duties, the software requires the following data:
- Information that helps to unambiguously identify the console computer, including its computer name, MAC addresses, OS build number and version.
- Network connectivity information, including the computer’s IP address, port, domain, and subnet.
- User identity information, including the names of any logged in users, and the name and password of any remote consoles.
Mobile Device Management (iOS) is an iOS app that enables the Cloud Console to communicate with, monitor, and control iOS devices. To perform its duties, the software requires the following data:
- Information that helps to unambiguously identify the device, including its name, model, serial number, build version, and UDID.
- OS version information to help determine what capabilities the device possesses.
- Location data used to track the device’s whereabouts.
- Information regarding device configuration, including whether the device is supervised, whether it has an active iTunes account, and which of the following features are enabled: voice roaming, data roaming, personal hotspot, device locator, do not disturb, activation lock, cloud backup, and passcode protection.
- Information regarding installed apps, including name, version, ID, app size, and the size of any app data files.
- Security information required to send the device push notifications, including its token, unlock token, and push magic.
- Additional information including battery level, phone number, last backup date, Wi-Fi MAC address, IMEI number, available cellular technologies, current and home carrier networks, roaming status, hardware encryption capabilities, and device capacity.
Mobile Device Management (Android) is an Android app that enables the Cloud Console to communicate with, monitor, and control Android devices. To perform its duties, the software requires the following data:
- Information that helps to unambiguously identify the device, including its name, model, serial number, build version, and Android ID.
- OS version information to help determine what capabilities the device possesses.
- Location data used to track the device’s whereabouts.
- Information regarding device configuration, including which of the following features are enabled: voice roaming, data roaming, personal hotspot, device locator, do not disturb, activation lock, and passcode protection.
- Information regarding installed apps, including name, version, ID, and app size.
- Additional information including battery level, phone number, last backup date, Wi-Fi MAC address, available cellular technologies, current and home carrier networks, SSID of currently connected WI-FI network, roaming status, hardware encryption capabilities, and total and available device capacity.
Power Save is energy management software that reduces power consumption by fine-tuning when and how computers power down. To perform its duties, the software requires the following data:
- Hardware profiles, including computer and monitor make and model.
- Information regarding events, including event IDs (sleep, wake, etc.) and their timestamps.
- Preferred interface language.
- Power Save Mac requires additional computer identity information, including IP and MAC addresses, machine name, machine ID, NetBIOS name, IP adaptors, OS information, and domain DNS.
Software Updater automatically downloads and applies updates to software on the computer, even if Deep Freeze is installed. To perform its duties, the software requires the following data:
- Information regarding the computer’s software license.
- Information regarding the programs Software Updater is meant to update, including their installed version and architecture (32 bit / 64 bit).
Usage Stats assists IT staff in determining how computers are utilized (or underutilized) by tracking and reporting computer usage. To perform its duties, the software requires the following data:
- An inventory of the computer’s installed products.
- Information regarding user activity, including who is currently logged in, who has used the computer in the past, the times that users logged in and out, and what user-facing executables were launched by those users.
UserVoice is a user feedback utility incorporated into the Deep Freeze Cloud console. To perform its duties, the software requires the following information:
- User identity, including first name, last initial, and email address.
- Details of the user feedback.
WINSelect applies restrictions to what operations can be performed within the Windows operating system. To perform its duties, the software requires the following data:
- An inventory of the files and features that the software could deny users access to, including available printers, control panel applets, drives, file extensions, desktop icons, and executables within the Program Files folders.
- Information to assist the software to deny access to selected browser features, including the version of Internet Explorer or Firefox installed on the computer.
